Protecting your privacy and data
The Zoni team understands how important your data is and we’re committed to making sure that the reliability of our services and the security of your information is crucial to our services.
Secure cloud software events dashboard
Our user focused cloud dashboard is designed for system administrators and employees alike, working across multiple events.
Zoni is delivered with security minded principles – permission based access, encryption of data and security of infrastructure.
Your data is stored securely and can only be accessed by people you give authority for viewing logs, exporting reports or connecting to other systems with our integrations.
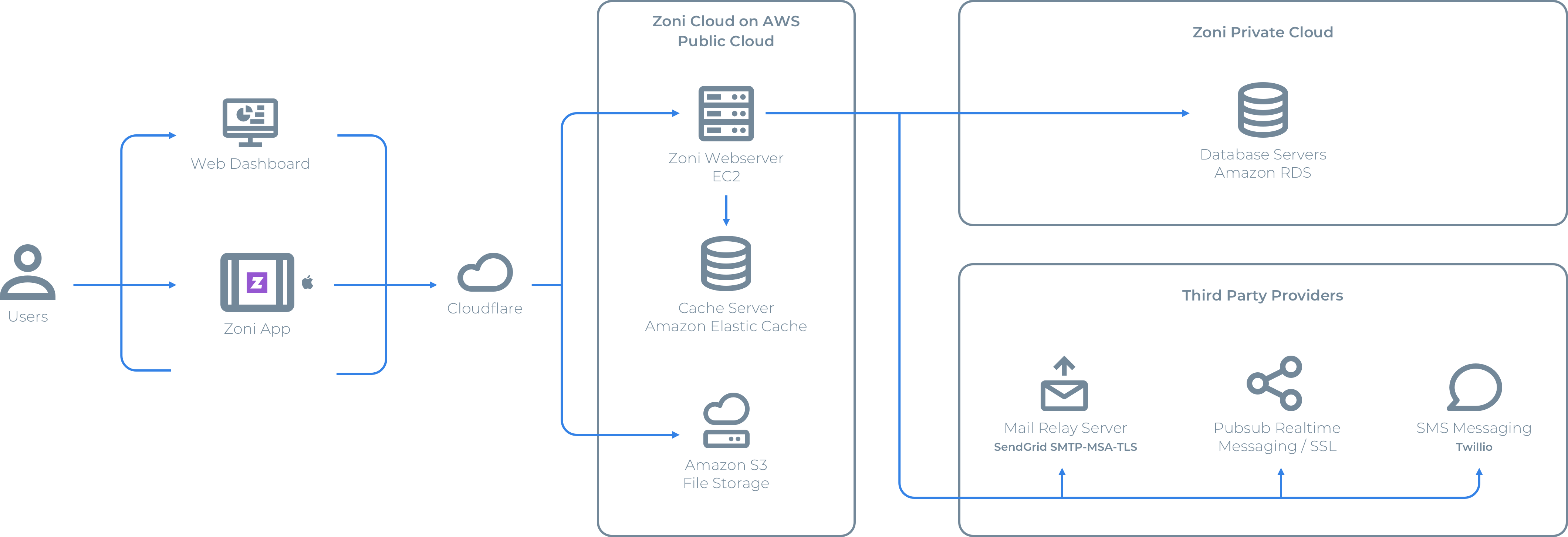
System security architecture you can rely on
Zoni customer data is securely transferred using HTTPS (industry grade SSL connection) across the Zoni kiosk app, Zoni dashboard and the secure cloud and servers. At rest, data is encrypted using AWS encrypted databases and AWS S3 Server-side Encryption. Zoni ensures protection against denial-of-service (DoS) attacks using CloudFlare’s advanced DDoS protection.
Zoni Product
Network & Application
Zoni supports your event data, guests data, employee data and subscription payment information. Including critical information about your visitor processes, the security of the this sensitive data and any billing settings needs to be water-tight.
Zoni’s system stores sensitive information and frequently collects personal information as well, such as names, emails, phone numbers and so on. You owe your customers the promise that their data will be handled safely and securely and will never be shared without their consent.
Employee Training
Zoni’s employees are highly skilled and trained in all aspects of the Zoni platform and are trained in many levels of data security and handling sensitive customer data. From both system level and local level security, our staff ensure your data and your customers and guests data are paramount to all our security efforts.
Passwords
Our promise of security extends from the very system that handles customer data and sensitive payment information. In-depth security processes, systems and methods are an essential part of our organisation. This is evident in our product, service delivery, facilities and security first mindset. Additionally, our security has been tried and tested against third parties as part of quality and control.
We continuously look for opportunities to make improvements and give you a highly secure, scalable system to provide a great arrival experience to your visitors. Zoni lets you deliver a secure guest experience at different levels by,
- Securing personal information
- Securing payment information
- Ensuring your data that rests with Zoni follows adherence standards.
- Network Security policies we follow within the Zoni internal network
Administration
Zoni ensures that only employees with a high level of training are able to gain access to administrative services for the sole reason to support and assist our customers. Our administrator accounts have different levels of permission so that data privacy and integrity are maintained and no employee should have access to data and features not relevant to their roles, responsibilities and obligations.
Regulatory Obligations
At Zoni, we take data integrity and security very seriously. Due to the nature of the product and service we provide, it is important we acknowledge our responsibilities both as data controllers as well as a data processors.
We store and process your data and that of your visitors with care and help you be compliant so that you can continue to build trust while enhancing customer experiences.
We help you assure your visitors that their data is and will always be secure. The promise of security is based on the very system that handles all payment, billing, subscription, and customer data and is an essential part of our product, processes, and team culture.
Our physical facilities, processes and systems are reliable, robust and third-party tested. We continuously look for opportunities to make improvements and give you a highly secure, scalable system to provide a great visitor management experience to your customers.
Zoni lets you deliver a secure event experience at different levels by,
- Securing your customer’s personal information and any associated payment information: compliance with PCI and GDPR.
- Ensuring Internal Data security of your data that rests with Zoni: adherence to ISO, SOC 1 & SOC 2, and MFA standards.
- Network Security within Zoni: Network, application and operational level security policies that we follow.
Data Hosting
ISO 27001 (formally known as ISO/IEC 27001:2013) is a specification for an information security management system (ISMS). An ISMS is a framework of policies and procedures that includes all legal, physical and technical controls involved in an organisation’s information risk management processes with the aim of keeping information secure.
With ISO’s robust information security management system (ISMS) in place, you gain the additional reassurance that a full spectrum of security best practices are implemented across the organisation.
Zoni is committed to identifying risks, assessing implications and putting in place systemised controls that inspire trust in everything that we do – from our codebase to physical infrastructure to people practices.
Physical Security
Zoni complies with the EU-U.S. Privacy Shield and U.S.- Swiss Privacy Shield by adhering to the principles of protecting the rights of anyone in the EU whose personal data is transferred to the United States as well as bringing legal clarity for businesses relying on transatlantic data transfers.
Network Security
The General Data Protection Regulation (GDPR) is a European privacy law that became enforceable on May 25, 2018. The GDPR replaces the EU Data Protection Directive, also known as Directive 95/46/EC, and is intended to harmonize data protection laws throughout the European Union (EU) by applying a single data protection law that is binding throughout each member state.
Zoni’s GDPR Commitment
The core of Zoni’s operations relies on the protection of our customer’s data. We only collect and store information that is necessary to offer our service, and we do this with the consent of our customers. Our approach toward privacy, security, and data protection align with the goals of the General Data Protection Regulations – GDPR.
Along with highly secure and robust system architecture, we have a variety of security measures in place to prevent unauthorised access and processing of personal data.
By setting up an internal compliance team (with functional heads) who worked with an external specialist from a global audit firm, our requirements were assessed and the required changes were rolled out including direct data privacy management functionalities for our customers.
Virtual Private Cloud
Zoni is supported by Amazon’s AWS platform and infrastructure. Zoni employees do not have any physical access to the production environment.
Details about security setup of AWS.
Cloud security is the highest priority at AWS. As an AWS customer, we are benefitted from a data centre and network architecture built to meet the requirements of the most security-sensitive organizations.
“Amazon has many years of experience in designing, constructing, and operating large-scale data centers. This experience has been applied to the AWS platform and infrastructure. AWS data centers are housed in non-descript facilities, with military grade perimeter control berms. Physical access is strictly controlled both at the perimeter and at building ingress points by professional security staff utilizing video surveillance, state of the art intrusion detection systems, and other electronic means. Authorized staff must pass two-factor authentication no fewer than three times to access data center floors. All visitors and contractors are required to present identification and are signed in. They are also continually escorted by authorized staff.”
In addition to physical security, being on the AWS platform also provides us significant protection against traditional network security issues on the infrastructure including,
- Distributed Denial Of Service (DDoS) Attacks
- Man In The Middle (MITM) Attacks
- Port Scanning
- Packet sniffing by other tenants
Zoni obtains the SOC 1 and SOC 2 report from AWS for the services rendered by them and validates the same for the effectiveness of the opinion of the third-party auditor.
Redundancy & Failovers
Zoni implements the use of two-factor authentication to grant access to our administrative operations including both, infrastructure and Zoni services. Administrative privileges are restricted to very few employees. Additionally, both application level roles and AWS roles are used to ensure only required operations are allowed for specific users.
Any Zoni administrative access is automatically logged and mailed to our internal security team. Detailed information on when/why the operations are carried out is documented and notified to the security team before performing any changes in the production environment.
Data Encryption
SSH keys are required to gain console access to our servers and each login is identified by a user. All critical operations are logged to a central log server and our servers can be accessed only from restricted and secure IPs.
Hosts are segmented and accesses are restricted based on functionality. That is, application requests are allowed only from AWS ELB and database servers can be accessed only from application servers.
Access & Permissions
Secure Access
Zoni’s application servers can be accessed only via HTTPS. We use industry standard encryption for data traversing to and from the application servers.
XSS
All user input is properly encoded when displayed to ensure XSS vulnerabilities are mitigated.
CSRF
All POST requests are checked for CSRF token before processing the request.
SQL Injection
We use prepared statements for database access to avoid SQL Injection attacks.
Encrypted Data Storage
We do not store sensitive card details on any Zoni network. The keys for various third party services (like payment gateway) are stored in our database in encrypted form.
Vulnerability Scanning & Patching
We periodically check and apply patches for third-party software/services. As and when vulnerabilities are discovered we apply the fixes. We do periodic vulnerability scanning using the services of an authorised QSA.
Zoni performs the VAPT assessment on a quarterly basis.
We use Amazon’s RDS for our database. The automated backup feature is configured for RDS.
We backup data for up to 30 days.
We have configured Amazon RDS in Multi-AZ which provides enhanced availability and durability. Each AZ runs on its own physically distinct, independent infrastructure, and is engineered to be highly reliable. Learn more.
Incident Responses
Zoni has a strict set of procedures in place for the monitoring, documenting and reporting of all incidents related to the delivery of services including but not limited to security breaches, whether successful or not, detection of attempted security breaches and the processes which we undertake to report these incidents to our internal security team, third parties as required by law and our customers.
Incident responses are part of our monitoring and uptime guarantees and at times we may disclose these publicly or to our customers by posting incident reports and responses on our website or through a third party authorised service for monitoring such incidents remotely.
Procedures & Policies
Zoni has a strict set of procedures and policies we abide by in order to deliver our services to customers. These apply to both the service, applications, network, security and customer standards we pride ourselves on delivering.
All Zoni employees are bound by these procedures and policies and agree to uphold them to the best of their abilities when carrying out their assigned roles, tasks and obligations.
Our procedures and policies extend to both service delivery, network, data and physical security.
Monitoring & Uptime
We use both internal and external monitoring services to monitor all Zoni services. Our monitoring system will alert the Operations & Security Team through emails and phone calls if there are any errors or abnormalities in the request patterns delivered by the service or failure to reach services for a specific period of time. At times we may publish this information to our customers so they may check our service status and hold us accountable to our service Terms of Service guarantees.
Disclosure
We are working continuously to make our system secure. If you find any security issues, please send it to support@zoni. We will make sure the issue is fixed and updated at the earliest. Please ensure you read our Terms of Service and Privacy policies carefully and that you fully understand them and agree to them before using the Zoni service.
Your organisations security is our highest priority.
INTEGRITY
Our easy to use cloud dashboard is designed for administrators working across multiple event locations. Built for working teams, assign users with permissions that give them access to the right tools for operating a more efficient event.
We store your data on secure cloud servers that can only be accessed by people you specify and those with data centre secure access levels. Your data is maintained with detailed logs that can be exported with just one click or direct integration to existing systems like Eventbrite.
Zoni is highly sought after for enterprise and government customers or those that require compliance with PCI, ITAR, DSS, and other regulatory frameworks when running their workplace and corporate events.

Australian Company
We are a technology company based in Australia and specialising in Visitor Management software and applications.

Amazon Web Services
You expect the best and we rely on the best with cloud hosting and security provided by Amazon AWS Australia.

Fanatical Support
Zoni offers extensive online guides and assists customers with setup and ongoing top tier support staff
Try Zoni for Free
Zoni offers a 100% free trial so you can test all the features at zero cost with no credit card required to start today!